Suddenly, they reemerged with a bang.
The new evidence surfaced during a police investigation in the Netherlands.
Acryptocurrencytheft had been reported to the Dutch National High Tech Crime Unit (NHTCU).

On the victims server, the cybercops found a familiar foe: Ebury.
The discovery revealed a new target for the botnet.
Ebury had diversified to stealing Bitcoin wallets and credit card details.
Back in 2014, the ESET researcher had co-authoreda white paperon the botnet operations.
He called Ebury the most sophisticated Linux backdoor ever seen by his team.
40% off TNW Conference!
According to US officials, the operation fraudulently generated millions of dollars in revenue.
A year after ESETs original paper was published, an alleged Ebury operator was arrested in Finland.
His name was Maxim Senakh.
The Finnish authorities then extradited the Russian citizen to the US.
The 41-year-old eventually pleaded guilty to a reduced set of computer fraud charges.
In 2017, he was sentenced to nearly four years in prison.
In apress release, the US Justice DepartmentsaidEbury had infected tens of thousands of servers across the world.
Yet that was just a fraction of the total.
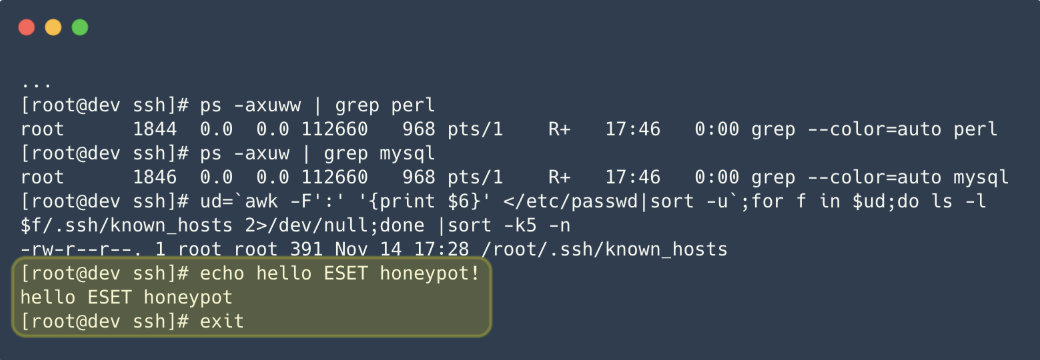
Hello ESET honeypot
While Senakhs trial progressed, ESETs researchers ran honeypots to track Eburys next moves.
They discovered that the botnet was still expanding and receiving updates.
But their detective work didnt stay concealed for long.
It was getting more and more difficult to make the honeypots undetectable, Leveille says.
They had a lot of techniques to see them.
One honeypot reacted strangely when Ebury was installed.
The botnets operators then abandoned the server.
They also sent a message to their adversaries:Hello ESET honeypot!
As the case went cold, another one was developing in the Netherlands.
By late 2021, theNHTCU had created another lead for ESET.
Working together, the cybercrime unit and cybersecurity firm investigated Eburys evolution.
The botnet had grown, Leveille says.
There were new victims and even larger incidents.
ESET now estimates that Ebury has compromised about 400,000 servers since 2009.
In a single incident last year, 70,000 servers from one hosting provider were infected by the malware.
As of late 2023, over 100,000 servers from one hosting provider were still compromised.
Some of these servers were used for credit card and cryptocurrency heists.
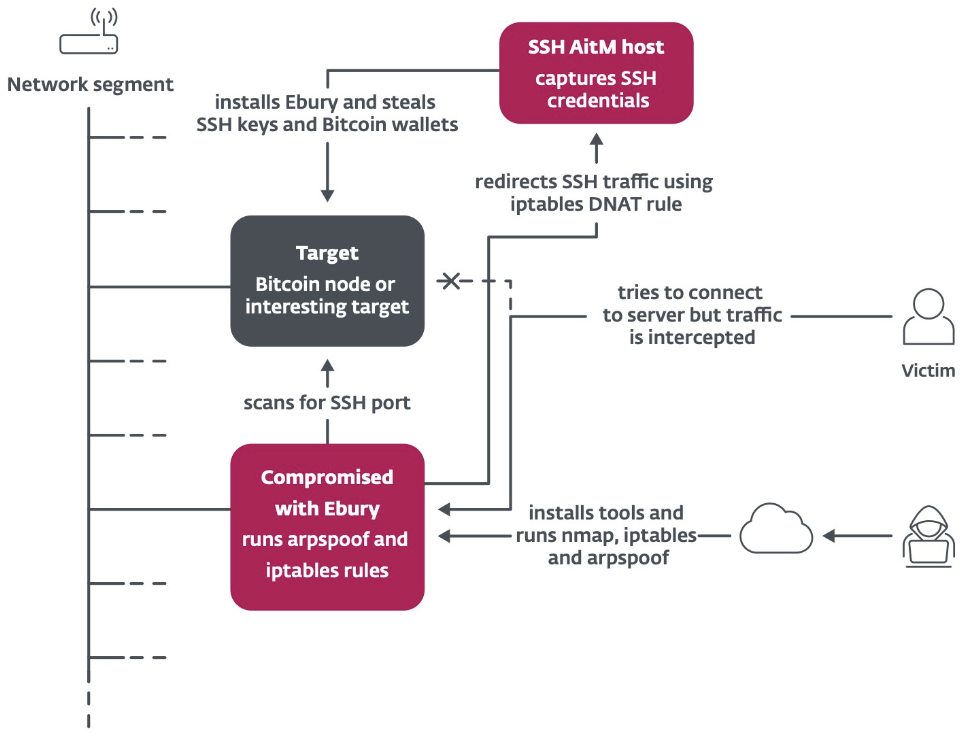
By applying AitM, the botnetintercepted online grid traffic from interesting targets inside data centres.
The traffic was then redirected to a server that captured the credentials.
The hackers also leveraged servers that Ebury had previously infected.
When these servers are in same internet segment as the new target, they provide a platform for spoofing.
Among the lucrative targets wereBitcoinand Ethereum nodes.
Once the victim entered their password, Ebury automatically stole cryptocurrency wallets hosted on the server.
The AitM attacks provided a powerful new method of quickly monetising the botnet.
Cryptocurrency theft was not something that wed ever seen them do before, Leveille says.
The Dutch investigation continues
The variety of Ebury victims has also grown.
They now span universities, small businesses, large enterprises, and cryptocurrency traders.
They also include internet service providers, Tor exit nodes, shared hosting providers, and dedicated server providers.
To conceal their crimes, Ebury operators often use stolen identities to rent server infrastructure and conduct their attacks.
These techniques have investigators in the wrong directions.
Theyre really good at blurring the attribution,Leveille says.
The NHTCU found further evidence of the obfuscation.
Ina new ESET white paper, the Dutch crimefighters highlightedseveral anonymisation techniques.
Eburys digital footprints often proved to be faked, the NTCU said.
The tracks frequently led to (seemingly) innocent people.
Consequently, they can create a cybercriminal cover pointing in other directions than themselves.
Its not closed, but Im not sure about any individuals behind it, he says.
Thats still an unknown for me at least.
Story byThomas Macaulay
Thomas is the managing editor of TNW.
He leads our coverage of European tech and oversees our talented team of writers.
Away from work, he e(show all)Thomas is the managing editor of TNW.
He leads our coverage of European tech and oversees our talented team of writers.
Away from work, he enjoys playing chess (badly) and the guitar (even worse).