They were installing chargers at apartment buildings in underground parking garages.
However, this is a space where its challenging to gain Wi-Fi internet connectivity.
They did this reluctantly for an early customer, yet wanted a better solution.

It’s free, every week, in your inbox.
You could find yourself stranded, unable to charge your car.
So we had to innovate.

The company calls it the worlds first No Internet for Things.
Im always interested in the answer to the question Why now?
The companyraised $14 millionin seed and VC funding earlier this year.
The token is time-bound, which means it dissolves after use.
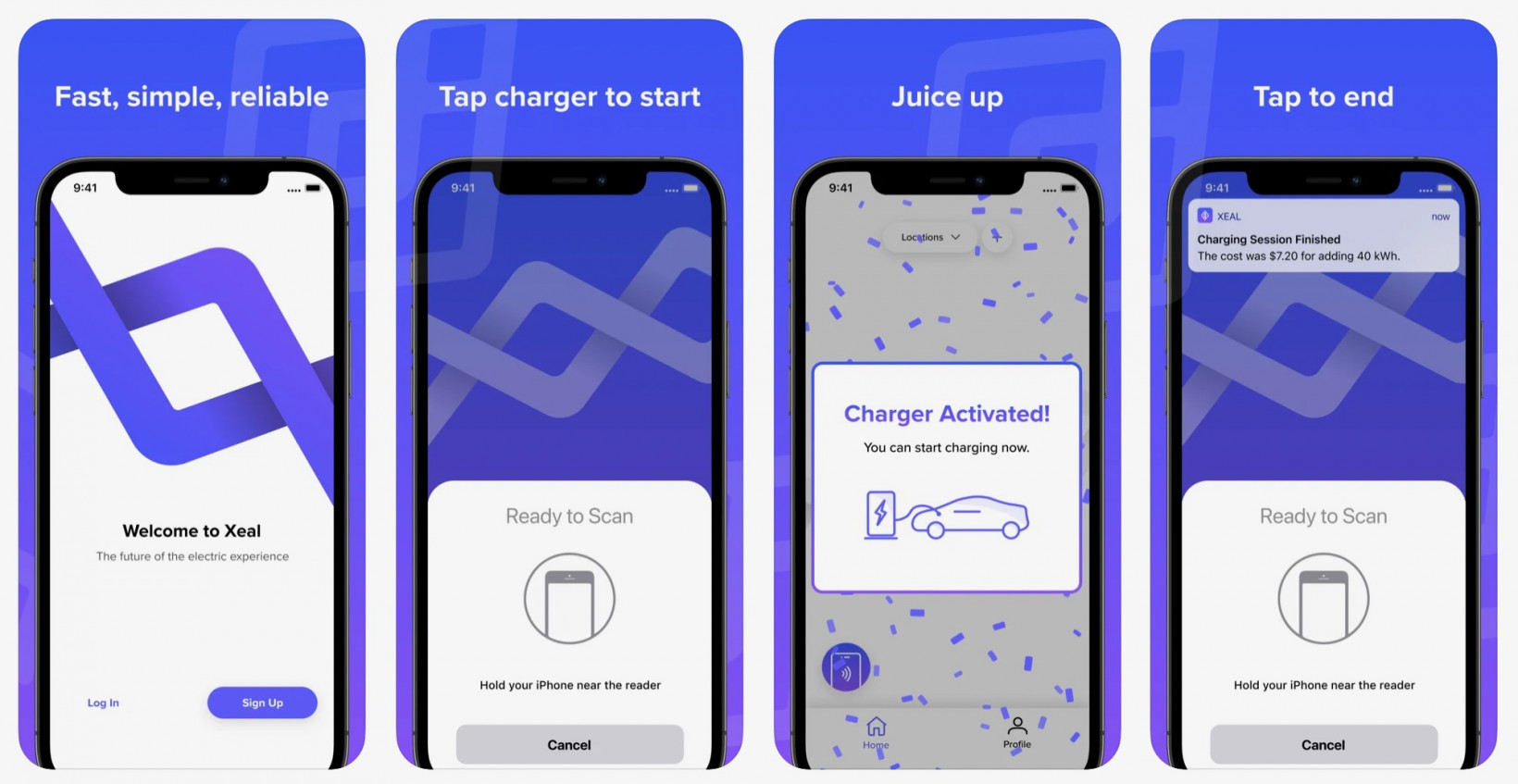
To charge your car, you hold your phone up to the charger.
Your mobile reads the cryptographic token, automatically bringing up anNFCscanner.

All of this is without Internet access its a closed-loop system without SIM cards or ethernet cables.
So, why cant you just use NFC without blockchain?
The blockchain, or specificallythe distributed ledger, is used to record the specifics of the charging session.
As Bharadwaj explained:
We need to know how long they were there and how much energy they consumed.
When the person finishes charging, they tap their phone to the charger to end the session.
This is essentially a delayed gateway.
Your phone is the gateway to the cloud.
And all the processing happens in the background.
The user never has to pop launch the app.
Its all done in the background.
When the user next accesses WiFI, the user gets another token.
This includes instances where users may not have tapped to end or if your phone dies.
Security
One of themost significant pain points for EV charging is security.
EV chargers are particularly vulnerable to man-in-the-middle attacks.
These are cyberattacks where an attacker relays or alters communication between two parties.
This enables the attacker to relay communication, listen in, and even modify what each party says.
Cybercriminals use these attacks to access personally identifiable information and steal credit card information.
Last year, security researchers SwRI developed a man-in-the-middle equipment that spoofed signals between a charger and vehicle.
It could overcharge and undercharge the battery, potentially resulting in big safety problems.
Were not going anywhere outside of the charger and the phone.
Further, these records are resistant to malicious changes by a single party.
I find Xeal interesting as they hit a critical intersection that has emerged not only for EV charging.
As more devices connect to the Internet and machine-to-machine interactions become mainstream reliable connectivity is crucial.
According to Bharadwaj that company has also attracted interestfrom shared mobility escooter and smart door lock companies.
This is the second part of a series Im writing about Web 3.0 and blockchain technology in mobility.
Im attempting to reduce the jargon and focus on the problems the tech aims to solve.
Story byCate Lawrence
Cate Lawrence is an Australian tech journo living in Berlin.