Disclaimer: This post is for educational purposes only.
Do not perform similar activities without explicit permission.
On April 30th, 2021, I rickrolled my high school district.

Not just my school but the entirety of Township High School District 214.
Its the second-largest high school district in Illinois, consisting of 6 different schools with over 11,000 enrolled students.
With that said, what we did was very illegal, and other administrations may have pressed charges.

We are grateful that the D214 administration was so understanding.
I didnt understand basic ethics or responsible disclosure and jumped at every opportunity to break something.
So obviously, I became curious about the technology at my high school.

And by curious, I mean port scanning the entire IP range of the internal district online grid.
I had a few friends help out with this project and oh boy, did we scan!
From the results, we found various devices exposed on the district online grid.
These included printers, IP phones… and even security cameras without any password authentication.
This is where I state the disclaimer again: never access other systems in an unauthorized manner without permission.
Exterity IPTV System
Before moving on, I will briefly explain the IPTV system.
The system is composed of three products:
AvediaPlayers are small blue boxes that connect to projectors and TVs.
These receivers include both a web interface and an SSH server to execute the serial commands.
Next, AvediaStream encoders connect to devices that broadcast live video.
They encode the live feed coming from these devices to the AvediaPlayer receivers, which display the stream.
Encoders are attached to computers that need to broadcast a stream, such as text carousels or morning announcements.
These also have embedded software similar to the AvediaPlayers.
Last but not least, AvediaServers allow administrators to control all receivers and encoders at once.
These have typical x86_64 processors and fire off the enterprise Linux distribution, CentOS.
Like the receivers and encoders, they also have web interfaces and SSH servers.
Since freshman year, I had complete access to the IPTV system.
Up to this point, in-person instruction was opt-in, with most students staying remote, including myself.
But in March, the superintendent announced that in-person instruction would switch to an opt-out model on April 5th.
A few days later, I decided to share my thoughts with a few close friends.
I gathered a small team across the district and started preparing.
We began to refer to the operation as the Big Rick.
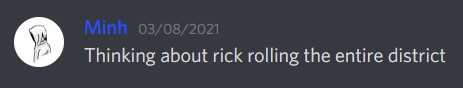
Instead, I used the SSH access on each receiver as the command-and-control (C2) channel.
This script contained various functions that could execute requests to the web interface locally on the receiver.
In the actual payload, I repeatedly looped commands to keep the rickroll running.
For example, every 10 seconds, the display would power on and set the maximum volume.
The only way to shut it off would be to pull the plug or change the input source.
(Looping input changes causes flashes even if the current source is the same as the latest source.
you could see this flash in the video at the 48-second countdown.)
The next issue we tackled was setting up a custom video stream to play the rickroll in real-time.
Setting up the stream was arguably the most time-consuming part of preparation because testing was an absolute pain.
So I tested at night instead.
Then, I would record a video to test if the projector displayed the stream correctly.
The lag you see in the video is one of the earlier issues I faced with the stream.
It turned out trying to redirect UDP traffic through the AvediaStream encoders added too much latency.
I fixed this by broadcasting to multicast directly from an AvediaServer usingffmeg.
Hopefully, I didnt scare any late-night staff!
The majority of the devices in this range were speakers found in hallways, classrooms, etc.
Similar to how AvediaPlayers linked to AvediaServers, each speaker connected to an EPIC server for their respective school.
These servers had a web interface locked behind a login page.
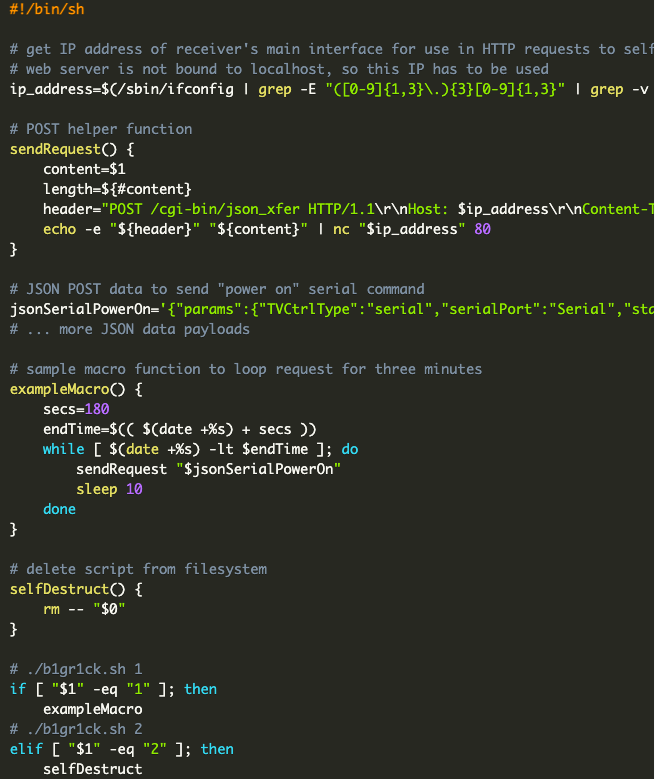
Only asingleEPIC server had default credentials configured.
We were able to modify the bell schedule at will, as well as upload custom audio tones.
We could change the bells to play Never Gonna Give You Up instead!
The credentials for this SMB server were the same default credentials for the EPIC system.
Each backup included an SQL dump of account usernames and password hashes.
Well, what if the other EPIC systems have backup servers as well?
And since these backup servers are separate from the EPIC servers, they might still use default credentials.
This scenario was precisely the case!
After some password cracking, we effectively had control over all the bell schedules in the district.
Another thing was that final exams were right around the corner.
The biggest concern was standardized testing, which wouldnt have breaks during passing periods.
We decided on April 30th, which was the Friday before AP exams started.
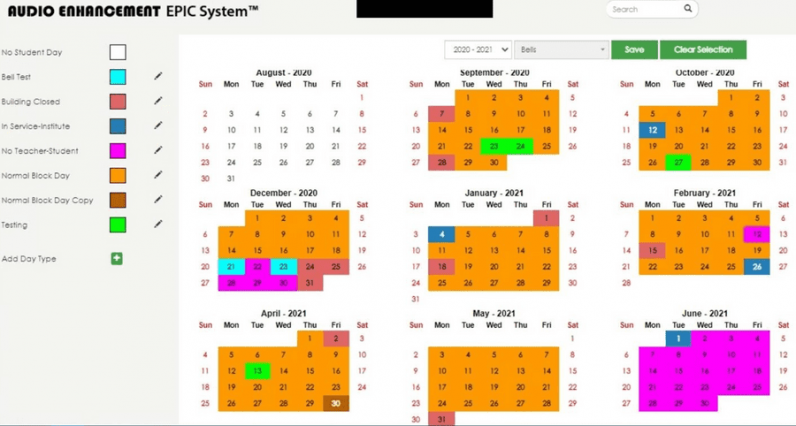
Below is the timeline of events on April 30th:
We also scheduled another modified bell for 3:25 PM.
The director stated that because of our guidelines and documentation, the district would not be pursuing discipline.
Later, he revealed the superintendents themselves reviewed and were impressed by our report.
I was ecstatic that the administration was open to remediating their problems and auditing them with us.
I had planned on announcing my involvement from the beginning since I wanted to publish this blog post.
(I was also pretty much the prime suspect anyways.)
But, just in case, I scheduled the debrief to take placeafterI graduated.
In all seriousness, the debrief went extremely well and was productive for everyone.
We answered clarifying questions from the tech team and gave additional tips for remediation.
Thats all and thanks for reading!