In the past few years, researchers have shown growing interest in the security of artificial intelligence systems.
Until now, backdoor attacks had certain practical difficulties because they largely relied on visible triggers.
Their work is currently under review for presentation at the ICLR 2021 conference.
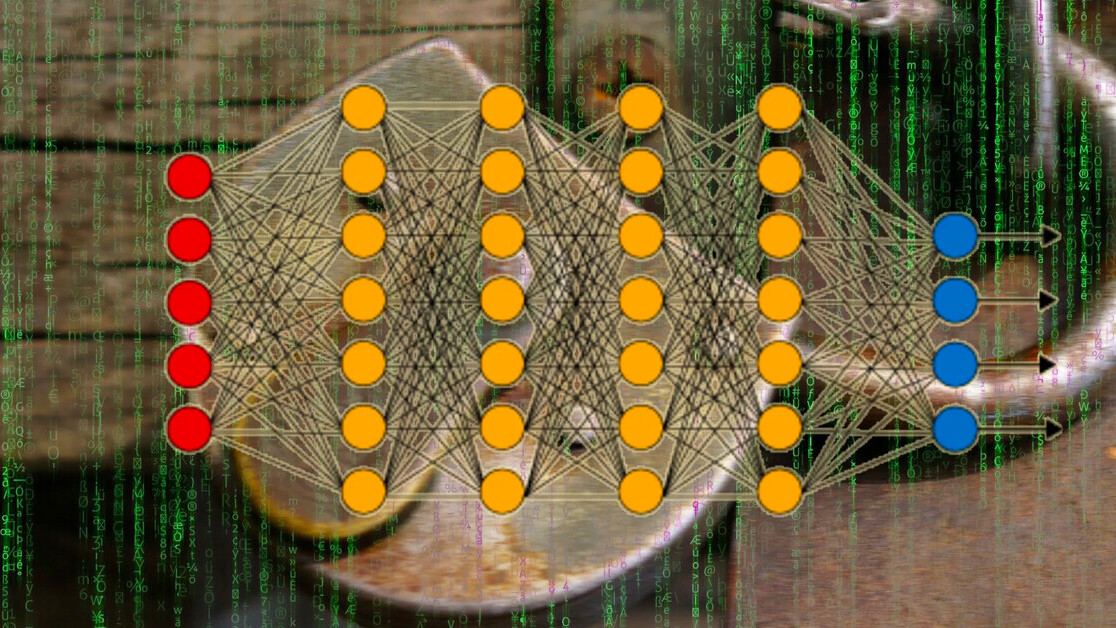
Most adversarial attacks exploit peculiarities in trained machine learning models to cause unintended behavior.
40% off TNW Conference!
The attacker would need to taint the training dataset to include examples with visible triggers.

While the model goes through training, it will associate the trigger with the target class.
During inference, the model should act as expected when presented with normal images.
During training, machine learning algorithms search for the most accessible pattern that correlates pixels to labels.

Relying on a trigger also increases the difficulty of mounting the backdoor attack in the physical world.
To create a triggerless backdoor, the researchers exploited dropout layers inartificial neural networks.
The attacker then manipulates the training process so implant the adversarial behavior in the neural web link.

This means that the data pipe is trained to yield specific results when the target neurons are dropped.
But as soon as they are dropped, the backdoor behavior kicks in.
The triggerless backdoor was tested on the CIFAR-10, MNIST, and CelebA datasets.

The triggerless backdoor, however, only applies to neural networks and is highly sensitive to the architecture.
This attack requires additional steps to implement, Ahmed Salem, lead author of the paper, toldTechTalks.
The probabilistic nature of the attack also creates challenges.
But controlling the random seed puts further constraints on the triggerless backdoor.
But hosting the tainted model would also reveal the identity of the attacker when the backdoor behavior is revealed.
you’ve got the option to read the original articlehere.