Making detailed datasets publicly available without violating anyones privacy is a critical challenge for projects like these.
It’s free, every week, in your inbox.
In this model, the data subject moves first, deciding what data to share.

Then the adversary moves next, deciding whether to attack based on the shared data.
The optimal strategy allows the data subject to share the most data with the least risk.
What other research is being done
Data managers usecryptographic techniquestoprotectbiomedical data.
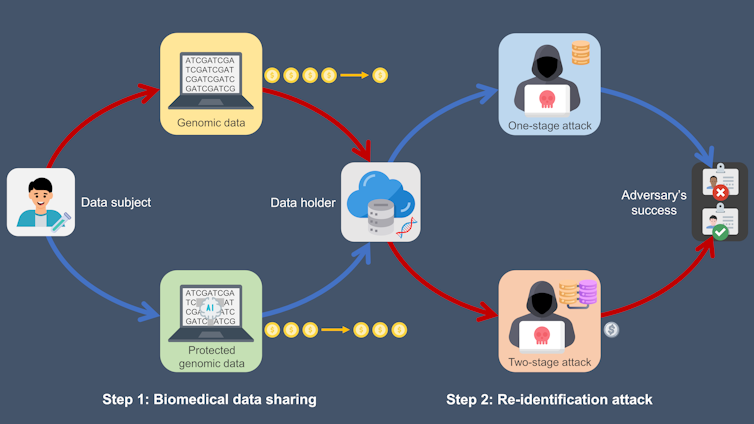
Other approaches includeadding noise to dataandhiding partial data.
