Before we dive into all that, heres a brief background about the technology and the issue.
What is Log4j?
It’s free, every week, in your inbox.

The logging software is used by companies to track activity on their servers (or even client-side apps).
This data related to activity can help companies solve any problem with their service.
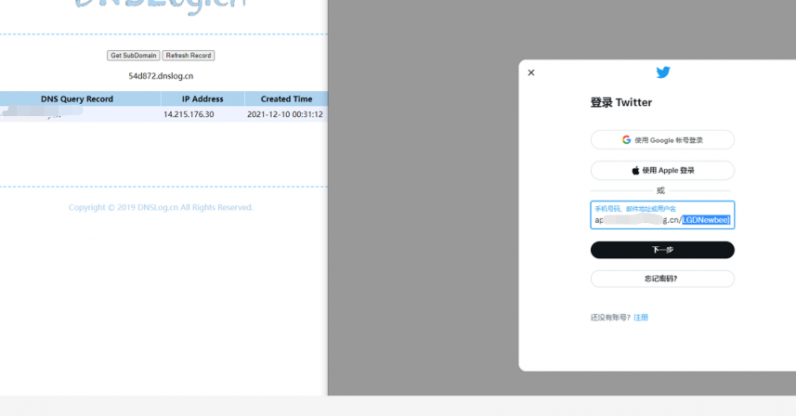
What is the Log4j bug?

The bug, listed underCVE-2021-44228last week, allows attackers to remotely execute code through a specially crafted string.
Since Log4j is so common, cybercriminals can easily manipulate log strings and control the server or the client.
If you want to read a detailed explanation of the issue in simple language, readthis Twitter thread.
Whos affected?
To be honest, I shouldve named this section Whos not affected?
Importantly, asArs Technicanoted, many of these companies have several lines of defense against cyber attacks.
Working on how to do that safely now.
So your toaster could be a hacking target too (?).
Data security platform LunaSec has a lengthy technical explanation about the impact of the bugon its blog.
It warned that people running third-party game clients might have to wait for the provider to patch the exploit.
For server admins,severalsecurity blogshave detailed guides for mitigations strategies.
Apache hasreleased version 2.16.0 of the Log4j framework.
This update completely removes message lookups to reduce the threat.
Plus, it has also disabled automatically resolving lookups contained in a message or its parameters.
The danger is looming over our heads.
Microsofts threat intelligence team has noted that many attackers are usingthe Colbat Strike penetration detection toolfor credential theft.
This was quickly followed by attempts to install coin miners, including the Kinsing miner botnet.
Self propagating with the ability to stand up a self hosted server on compromised endpoints.
Security researchers found out last night that the Log4J bug can affect all java versions.
So even if youre running an updated Java version, you should probably patch your Log4j service.
Just added support to LDAP Serialized Payloads in the JNDI-Exploit-Kit.
This is the maintainer who fixed the vulnerability that’s causing millions(++?)
of dollars of damage.
Its visibility.
We all know the landmines are out there but we cant see them.
He alsonotedthat ideally, the industry should fund teams that maintain three to four projects.
This is going to sound blunt, but it’s a distribution problem not a funding problem.
Corporations have budget and are willing to spend, but it takes too much time.
Thats a sad state of affairs.
But perhaps they might go back to sleep if the bug doesnt cause much damage.
I have to end this withan XKCD comicsumming up the situation.
That’s one heck of a mixed bag.
He likes to say “Bleh.
That’s one heck of a mixed bag.
He likes to say “Bleh.”